Sam Curry, a cyber security expert, revealed last week on Twitter that he and his team had found a security flaw in a service offered by SiriusXM Connected Vehicle Services. Various elements of convenience, security, and safety are made possible through the software suite known as SiriusXM Connected Vehicle Services, which is offered to connected automobiles. For instance, turn-by-turn directions, improved roadside assistance, remote door unlocking, remote engine starting, help to find stolen cars, automatic crash warning, or integration with smart home gadgets. More than 10 million vehicles in North America are thought to use SiriusXM’s connected vehicle services, including models from Acura, BMW, Honda, Hyundai, Infiniti, Jaguar, Land Rover, Lexus, Nissan, Subaru, and Toyota.
Hyundai issues
The MyHyundai and MyGenesis mobile apps from Hyundai and Genesis let authorized users start, stop, lock, and unlock their cars.
The researchers intercepted the two apps’ traffic, examined it, and were able to extract API requests for more research.
They discovered that the user’s email address, which was present in the JSON body of POST requests, is used to validate the owner.
The investigators then found that while registering, MyHyundai did not request an email confirmation. Using the target’s email address and an extra control character at the end, they made a new account.
Finally, they sent an HTTP request to Hyundai’s endpoint containing the spoofed address in the JSON token and the victim’s address in the JSON body, bypassing the validity check.
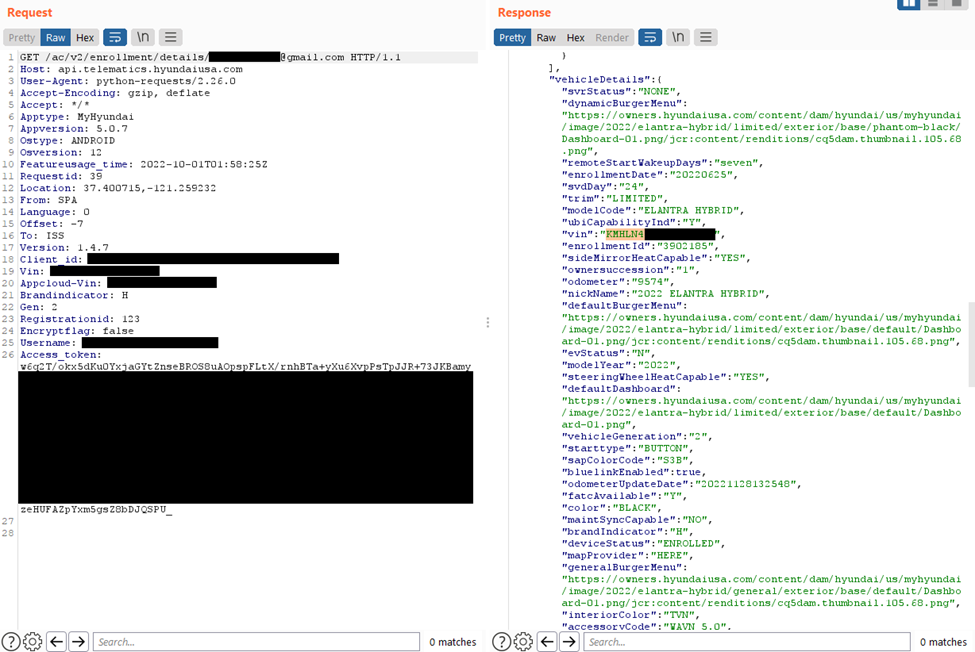
They attempted to unlock a Hyundai car used for the research to confirm that they could utilize this access to launch an assault on the vehicle. A little while afterward, the car’s door opened.
Eventually, the multi-step attack was built into a unique Python script that only required the target’s email address to launch the attack.
