
Mustang Panda
Mustang Panda is a China-based cyber espionage threat actor that was first observed in 2017 but may have been conducting operations since at least 2014. Mustang Panda has targeted government entities, nonprofits, religious, and other non-governmental organizations in the U.S., Europe, Mongolia, Myanmar, Pakistan, and Vietnam, among others.
Recently,the group has shifted from using archive files to using malicious optical disc image(ISO)files to deliver a modified version of the PlugX malware,increasing the group’s evasion against anti-malware solutions targeting Europe. The group employs a four-stage infection chain that leverages malicious shortcut (LNK)files and DLL search-order-hijacking to load the Plug X malware into the memory of legitimate software.
PlugX Malware execution flaw
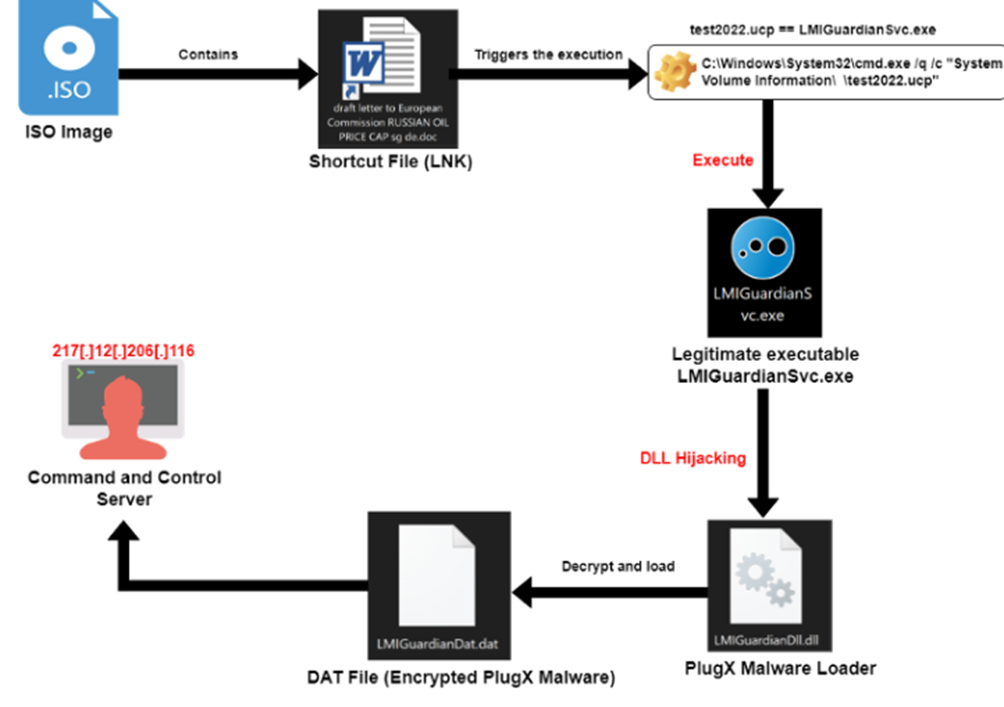
First Stage: PlugX Malware Delivered by ISO Image
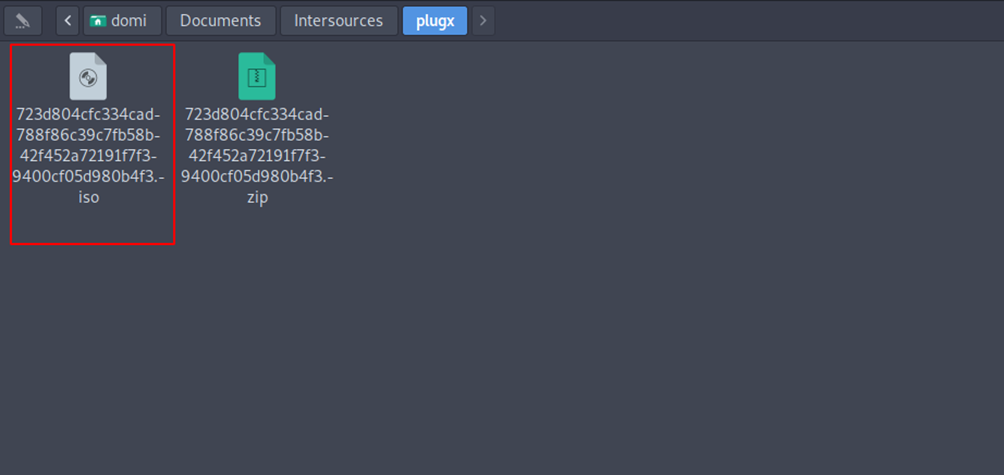
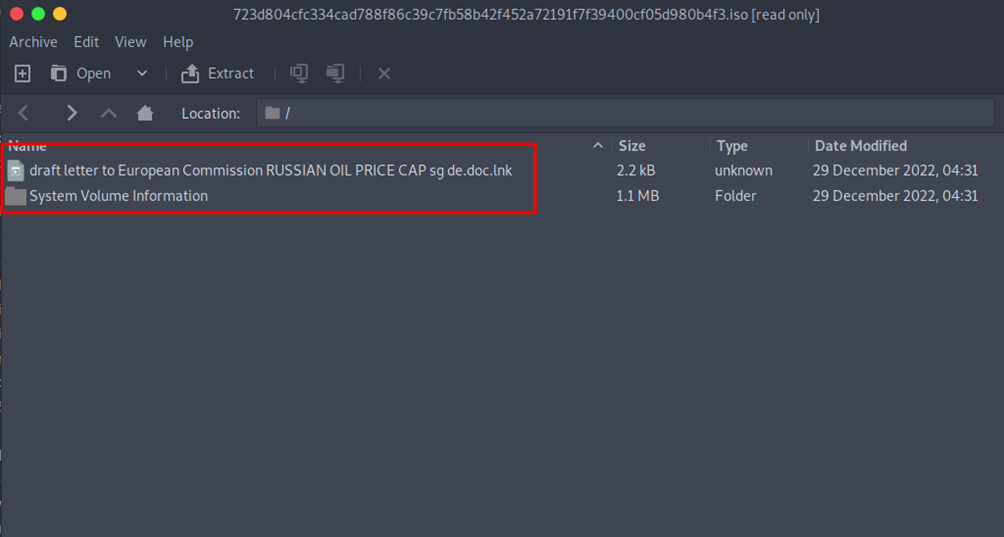
This ISO image contains Shortcut(LNK) file which looks like a doc file that contains malware.

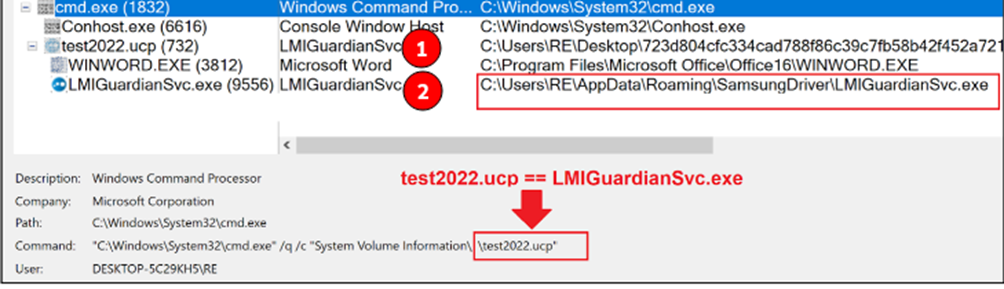
The tes2022.ucp can be replaced by the software from which you want to take the remote access of the victim system. The legitimate and malicious executable are placed on the same file path (System Volume Information) to perform DLL Hijacking.
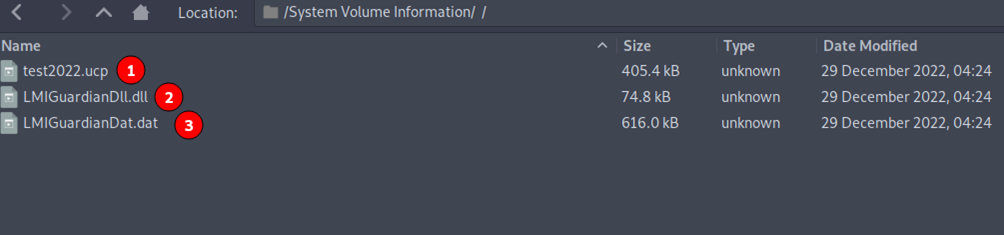
1. Legitimate software through which we replace the malicious exe.
2. Plugx loader
3. Encrypted Malware
Second Stage: DLL Hijacking Execution Chain to Load PlugX Malware
When a victim clicks on the shortcut file, it executes the command line argument mentioned in first stage, which is a technique called DLL hijacking (after the execution of LMIGuardianSvc.exe, it loads LMIGuardianDll.dll aka PlugX loader automatically). Upon execution of the PlugX loader a Microsoft Office Word document opens.
Process tree below shows that the execution of application takes twice and new directory is created which is use by malware to persistence in system.
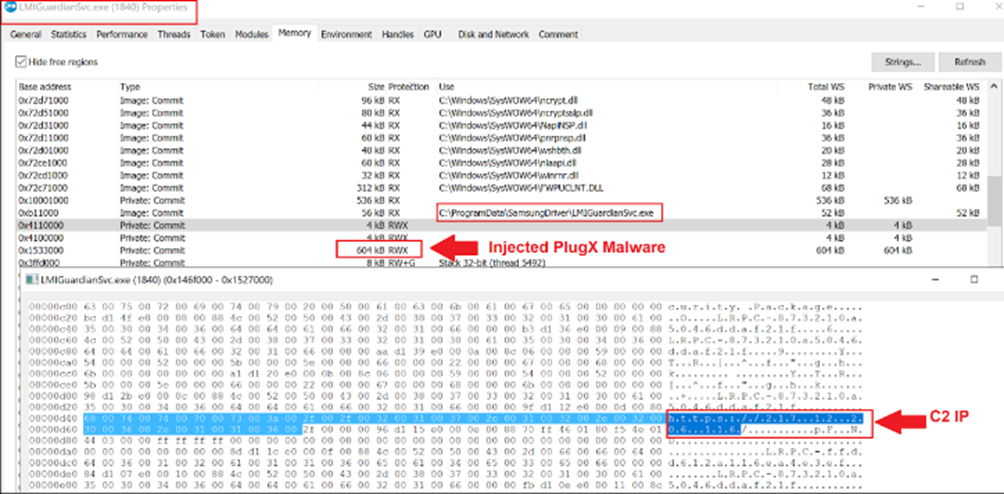
The PlugX Malware loader decrypts and loads the encrypted shellcode (LMIGuardianDat.dat) inside the LMIGuardianSvc.exe. Injected memory space can be extracted to perform further analysis of decrypted PlugX Malware.
During static analysis, Researchers identified that the PlugX malware loader used a simple XOR algorithm to decrypt the LMIGuardianDAT.dat (XOR encrypted PlugX shellcode) to avoid signature-based detection from antimalware solutions.
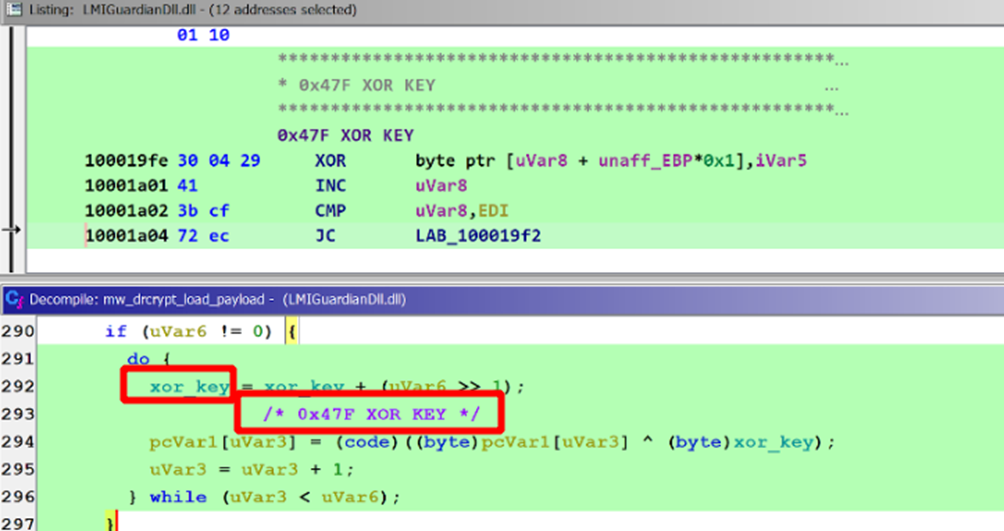
Dll uses 0*47F XOR key to decrypt the malware before executing.
Third Stage: Registry Run Key Persistence
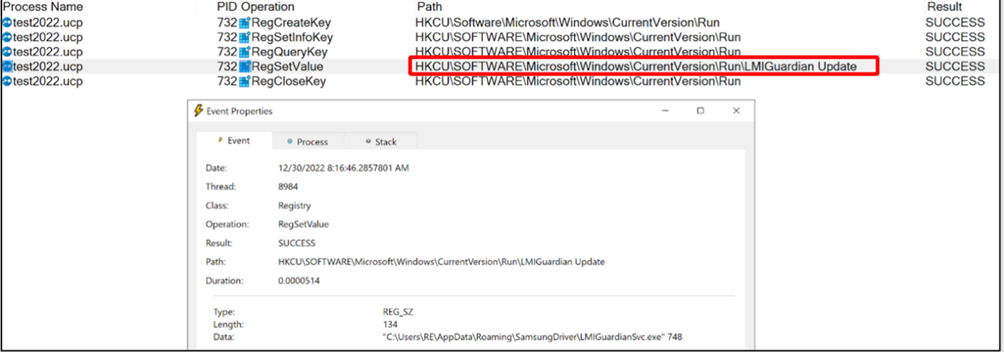
Threat group is abusing window registry run key to persistence in victim system. As you can see registry is update with a new run key called LMIGuardian Update.
Fourth Stage: Command and Control Connection
After a successful execution of PlugX malware, it connects to a remote C2 server which is used to send commands to compromised systems via the PlugX malware and to receive exfiltrated data from a target network.
Conclusion
Mustang Panda right now uses the Dll Hijacking technique to persist in the network. They are deploying there malware in Ukraine and Europe. They provide the doc file(.doc.lnk) which looks like a microsoft word document.
Mitigation
Implement basic incident response and detection deployments and controls like network IDS, netflow collection, host-logging, and web proxy, alongside human monitoring of detection sources.
- Employ host-based controls.
- Filter email correspondence and monitor for malicious attachments.
- Identify critical data and implement additional network segmentation and special protections for sensitive information, such as multifactor authentication, highly restricted access, and storage systems only accessible via an internal network.
- Create alerts for disk image file types, such as ISO, and shortcut files, which have been increasingly abused by different threat actors. Furthermore, organizations should consider disabling auto-mounting of ISO or VHD files.
- Configure intrusion detection systems (IDS), intrusion prevention systems (IPS), or any network defence mechanisms in place to alert on and upon review, consider blocking connection attempts from unrecognized external IP addresses and domains.
INDICATORS OF COMPROMISE
| Sample File Name(s) | SHA-256 Hash |
| LMIGuardianDll.dll | ee2c8909089f53aafc421d9853c01856b0a9015eba12aa0382e98417d28aef3f |
| LMIGuardianDat.dat | 8c4926dd32204b6a666b274a78ccfb16fe84bbd7d6bc218a5310970c4c5d9450 |
| draft letter to European Commission RUSSIAN OIL PRICE CAP sg de.iso | 723d804cfc334cad788f86c39c7fb58b42f452a72191f7f39400cf05d980b4f3 |
| draft letter to European Commission RUSSIAN OIL PRICE CAP sg de.doc.lnk | 2c0273394cda1b07680913edd70d3438a098bb4468f16eebf2f50d060cdf4e96 |
| LMIGuardianSvc.exe renamed (test2022.ucp) | 26c855264896db95ed46e502f2d318e5f2ad25b59bdc47bd7ffe92646102ae0d |
